This post is a “reprint†of an email we have just sent to the subscriber list for our Liberation newsletter. The audience is largely UK based businesses and public sector organisations. Should you wish to receive Liberation, you can subscribe here and please feel free to pass it on.
Today, Microsoft invite you to part with your hard-earned cash and upgrade your computers to Windows 7®. If you are one of the majority still using Windows XP, then moving to Windows 7 may not be a pleasant or inexpensive task…
Surprisingly there isn’t actually a way to upgrade your computer from Windows XP to Windows 7 in the traditional sense. You’ll need to back up all your data, re-format the hard-drive and start again from scratch.
Windows doesn’t store your documents, personal information, historical data, emails, passwords, cookies, preferences, settings etc. in one place. So backing up and rebuilding Windows computers is a very time-consuming and complicated process:
- Work our how many licenses you need then go and pay for them
- Buy some new storage for all the temporary backup space you’ll need
- Back up everything on every computer
- Install the basic operating system
- Find and install the right hardware drivers for your machine(s). Much hardware may not yet have suitable Windows 7 drivers
- Register and Activate each new computer, requires you to have network access
- Find all the disks and license keys for the applications you use, then re-install them. If they are still compatible that is
- Install & configure the drivers and software for printers and other peripherals. Many peripherals may also not yet have suitable drivers
- Copy your data and settings etc. back to all the right places on the new system.
Plan for this process taking anywhere between 4 and 8 hours for each and every computer you have.
Gartner estimates that real migration costs will be between $1,035 & $1,930 per user from Windows XP to Windows 7.
Why can’t I upgrade?
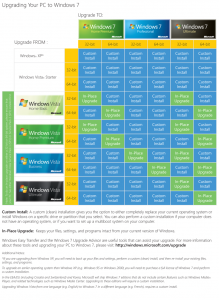
Windows 7 Upgrades
That is a good question, and one that we have not seen a good answer to. Walt Mossberg of the Wall Street Journal asked Microsoft about upgrade paths and was sent this matrix showing all the different ways you can’t upgrade from other versions of Windows to Windows 7 (Blue = No upgrade, rip out and replace. Green = in-place upgrade).
Microsoft have also provided a document explaining the same thing in words. There is no upgrade path from any of the following operating systems:
Windows 95, Windows 98, Windows Millennium Edition, Windows XP, Windows Vista® RTM, Windows Vista Starter, Windows 7 M3, Windows 7 Beta, Windows 7 RC, or Windows 7 IDS, Windows NT® Server 4.0, Windows 2000 Server, Windows Server® 2003, Windows Server 2008, or Windows Server 2008 R2.
That’s a complete mess. What can I do then?
You could do nothing and stay on Windows XP for as long as possible. Although we think this will be a very popular choice, staying on a nearly 10 year old OS probably isn’t the best policy for a forward thinking organisation.
You do have a choice

As you are going to have to rip out and replace your computers’ operating systems anyway, now is a real Carpe Diem opportunity to investigate an alternative (or two) whilst considering your options.
The Open Learning Centre recommends that your organisation investigates the many benefits offered by a modern Linux-based desktop operating system such as Ubuntu. As an authorised Ubuntu partner we can help your organisation with evaluation, installation, testing, migration, implementation, training and support services.

Ubuntu Desktop
Ubuntu is a modern, stable, reliable and secure computing platform that includes most of the applications we all use every day, such as a compatible office suite (Word-processing, Spreadsheets, Presentations) OpenOffice.org, email and calendaring, web browsing and image manipulation tools.
Best of all, Ubuntu is free:
Ubuntu is and always will be free of charge. You do not pay any licensing fees. You can download, use and share Ubuntu with your friends, family, school or business for absolutely nothing.
The retail price for a single Windows 7 Professional license is £219.99 and it’s £229.99 for the Ultimate version. This doesn’t include applications either.
Our Offer: On-Site Ubuntu Installation and Training
The Open Learning Centre will visit your premises, install Ubuntu on a suitable computer, and provide approximately 2-3 hours (i.e approx half a working day) of professional training and advice on Ubuntu for £229.991 (inc. VAT). An outline of the training is available on our website. Please contact us to book your Introduction to Ubuntu.
Open your mind to Open Source software today










